What Happened
At approximately 5:44 AM UTC on November 4th, an incident occurred involving the wrsETH market on Base. Due to an oracle malfunction, wrsETH collateral was drastically overvalued enabling an attacker to borrow millions in various assets using minimal wrsETH collateral.
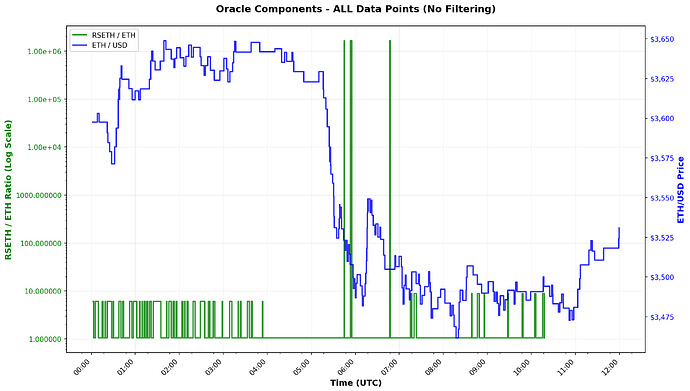
The protocol prices wrsETH using two Chainlink oracles: an ETH/USD oracle and a wrsETH/ETH oracle. To derive the USD price of wrsETH, the protocol multiplies these two feeds together. The issue originated from the wrsETH/ETH oracle, which erroneously reported that 1 wrsETH equals 1,649,934.60732 ETH—valuing a single wrsETH token at approximately $5.8 billion.
Notably, this was the same user responsible for the 10/10/25 exploit.
Attacker (contract): 0x42ecd332d47c91cbc83b39bd7f53cebe5e9734bb
Attacker (EOA): 0x6997a8c804642ae2de16d7b8ff09565a5d5658ff
ETH/USD oracle: 0x71041dddad3595F9CEd3DcCFBe3D1F4b0a16Bb70
wrsETH/ETH oracle: 0xd7221b10FBBC1e1ba95Fd0B4D031C15f7F365296
The first massive faulty reading from the wrsETH/ETH oracle occurred at precisely 5:44:55 UTC, and the attack was executed within 30 seconds of this malfunction.
Transaction Details
The attack started on block 37722875 with the first transaction (hash: 0x229caeb87e0b6c31afad950150d2ba05a8d7fe823c9e5c05af63b4150b8f6cc6) flash loaning 0.00065 wrsETH to withdraw 1.206M cbXRP. This was followed by a set of 11 transactions::
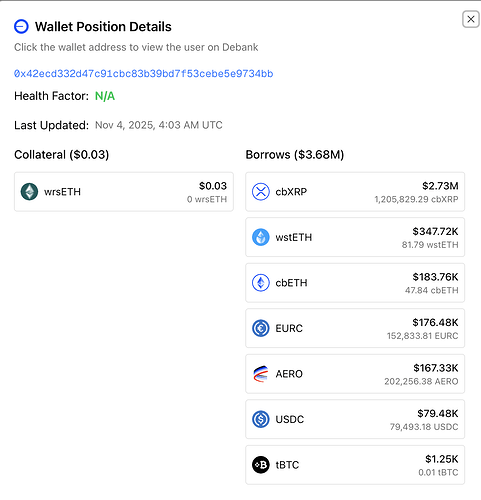
The borrowed tokens were atomically swapped to WETH in the same transaction and sent to the attacker’s original address (0x6997a8c804642ae2de16d7b8ff09565a5d5658ff). All of these transactions combined led to a total bad debt of $3.7M on Moonwell.
The address can be viewed on Debank here: 0x42ecd332d47c91cbc83b39bd7f53cebe5e9734bb
What We Did
Immediately following the exploit we zeroed out supply and borrow caps for wrsETH, effectively pausing activity in the wrsETH markets on both Base and Optimism. This ensures wrsETH can no longer be supplied or borrowed by any new users. We also reduced borrow caps in all markets on base and optimism (reducing them all to 0.1), temporarily pausing additional borrows across all markets. This is done to mitigate the risk of any previous wrsETH suppliers over-borrowing if the oracle continues to give incorrect prices. This restriction will be lifted once a fix to this oracle is in place.